
HTTPS is the secure means for exchanging information over the Internet today and widely accepted. HTTPS provides the ability of having the facility of HTTP added with SSL/TLS security at the respective layers which is used by almost all applications today over the internet to ensure secure transmission of their data. Almost all apps have implemented this to enable the secure channel of communication of their clients with their own server.
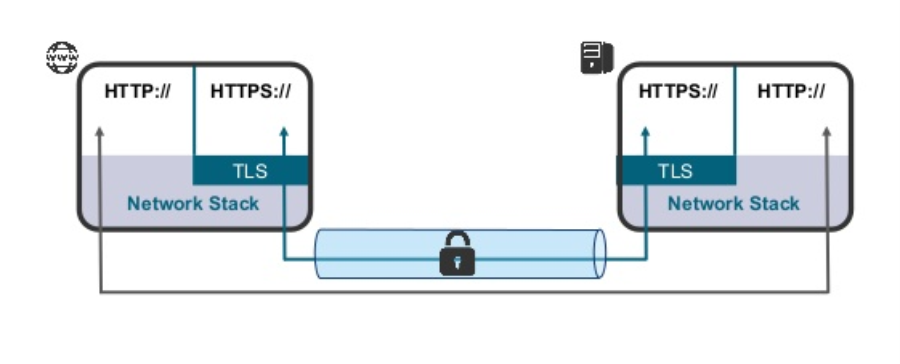
Interception of this secure HTTPS traffic is possible at various points but it is normally not possible to achieve the decryption of the HTTPS traffic due to the secrecy algorithms used for encryption of the data. It is very important to note that a large amount of criminals, terrorists or other anti-national elements are using this secure feature of HTTPS to have encrypted communication with their associates. Hence it is important for law enforcement agencies to have some means for intercepting the communications of such targets and being able to read the contents of HTTPS traffic of specific targets.
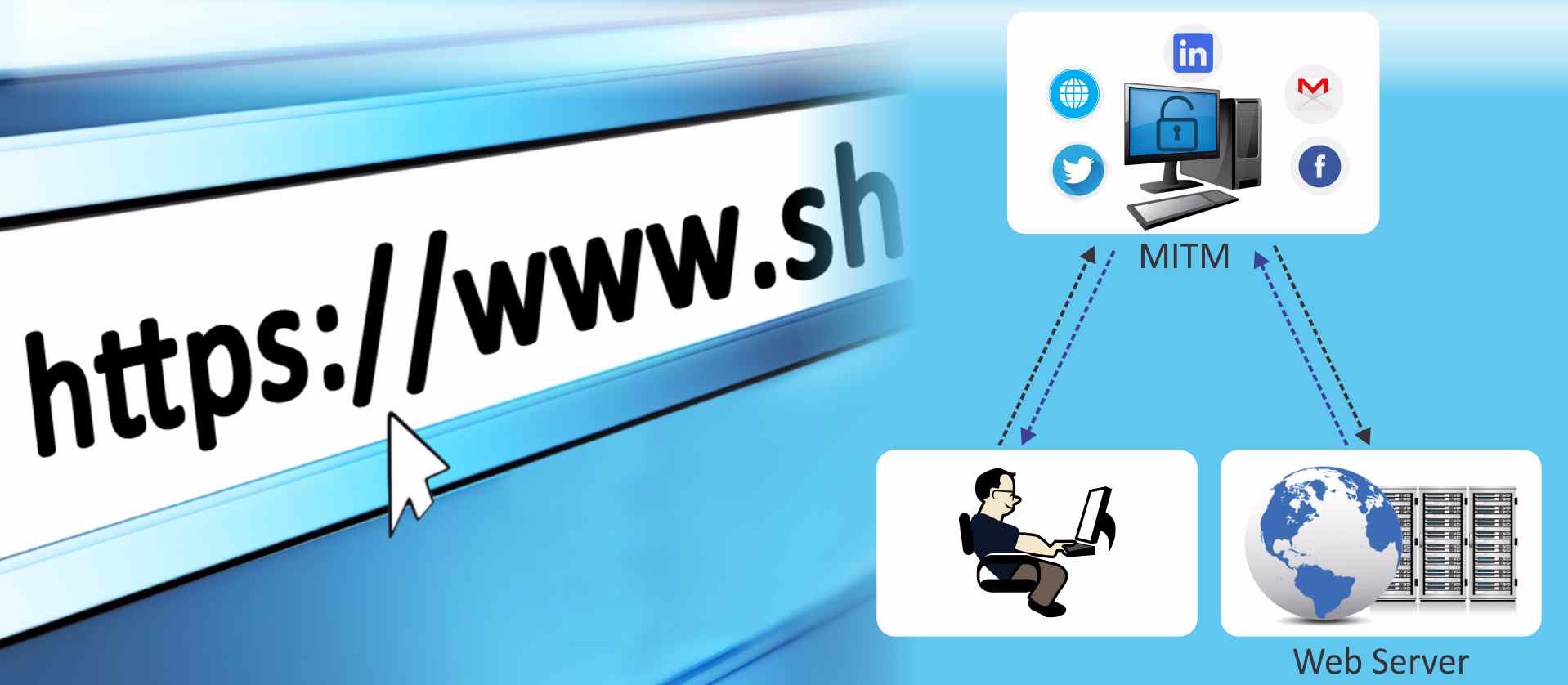
The security of this protocol is built on the use of trusted certificates which authenticate the server to the client and vice versa. The only way to overcome this and to be able read the data being transmitted would be the use of the Man-In-The-Middle (MITM) attack where the law enforcement agency is able intercept the traffic at suitable points where it replicates the server to the specific client and the client to the application server. It would involve the generation of a certificate by the National Certification Authority which has the jurisdiction for this within its own country. The law enforcement agency would use this national certificate which is acceptable within its own boundaries over the Internet. This is a difficult operation as all traffic will need to be filtered through this and then only traffic from the suspected target needs to be handled separately. The rest can be bypassed and work directly without any hindrance. HTTPS decryption of secure traffic from suspected targets can be achieved using this roundabout technique.
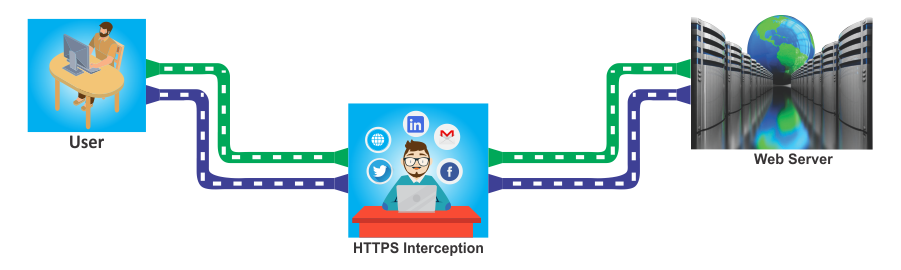
The MITM can be employed on systems like specific WiFi networks where the suspected targets could be working by combining this technique with a WiFi Monitoring System. This can provide a smaller system for targeted deployment at specific points where the target is present. The other method is to combine this with the lawful interception system deployed with the various Internet service provider locations. There would be a need for filtering out the traffic of only suspected mobile phones or other devices with specific IP addresses to carry out this process.
This can provide a means for carrying our decryption of HTTPS traffic of specific targets to be able to monitor their communications using secure apps.
